How fraudsters 'warm-up the shop' to commit gift card fraud
Fraudsters require patience to 'warm-up' stolen accounts to commit gift card fraud. Learn how it's done - and how to prevent fraud attempts.


In this post, we will show you how one of the more novel ways of committing fraud works in practice.
There are many types of fraud and even more methods to commit each of them. The problem for people fighting fraud is that they often don’t fully understand how fraudsters work - specifically, what they do, what tools they use, how they think, and what they search for. In the Dark web, you can find the answers to these questions, and with this post, we will bring the motives to light - and hopefully help merchants who fight fraudsters.
Here, you can find out how criminals connect card-not-present fraud with account takeovers and how they warm up the account to impersonate a typical customer. We have based our text on a tutorial on how to defraud electronic gift cards in one of the biggest e-commerce shops on the Internet.
Getting started with fraud
There are many types of fraud that pose a threat to e-commerce companies. One example is carding, where fraudsters use stolen credit cards to pay for merchandise. As a result, the merchant loses their products and has to pay chargeback fees to the rightful cardholder whose card was stolen. Another big problem is account takeover when a fraudster uses a stolen account for fraudulent purposes.
Stolen accounts can be used in many ways. For example, fraudsters can profit from accounts with a pinned payment method (credit card, Paypal, gift card, air miles, refund balance, etc.). Fraudsters use both a stolen credit card and a stolen account that belongs to the same victim.
How do fraudsters get card details?
In fraudster slang, there is something called logs. These are usually harvested by botnets from computers infected by malware. This way, hackers can gain useful data from computers, usually logs consisting of:
- Logins, usernames and passwords to accounts
- Credit card data (number, CVV, expiration date)
- Personal data such as ID scan
- Cookies
- Information about the compromised device (IP address, location, operating system - this data will be handy for fraudsters when they want to mimic the victim's behavior)
- Screenshots from the compromised device.
Logs are sold in dedicated shops on the dark web. Because of the extensive information within them, logs provide the highest success rate in carding and ATO. They are used by mid-level and highly experienced fraudsters who know how to use them effectively. Gathering resources is usually the first phase for criminals who want to commit fraud.
Logs are very handy for fraudsters because they contain a lot of useful information that helps them enact fraud. Login details to various accounts are valuable in themselves. Usually, it is credentials to all accounts that were used by device user(s). E-commerce accounts can be easily defrauded when they type a PIN into a payment method. Even if the account has no pinned payment method, it can be very convenient for fraudsters because it is easier to defraud an old account that already has a positive purchase history. This is why carders look for stolen e-shop accounts.
Email accounts are another lucrative target that fraudsters can access from logs. Currently, email accounts are at the core of our digital lives. We use them to register various accounts, reset passwords, receive invoices, communicate with banks and friends, and much more. Our email accounts are one of the biggest sources of information about ourselves. Interception of our email account could lead to many avenues of fraud - taking a loan out in our name, hijacking all accounts registered on this email account by resetting passwords, using phishing attacks against our friends from our contact lists, and so on.
Information from hijacked accounts connected with information from stolen social media accounts can also provide a lot of information that could help a fraudster imitate us during a scam attempt. For example, when a fraudster pretends to be us during calls to the bank. Sometimes fraudsters can find valuable scans of the victim’s documents saved as an email that could be used for authentication - or worse, it could be sold on the dark web. Each stolen account will hold its weight in gold for a fraudster.
Not only do logs contain a lot of technical data about stolen accounts, but on dark web markets, fraudsters can buy stolen accounts on cryptocurrency exchanges with much data that allows them to imitate account owners. This imitation isn’t perfect, and some details can be detected by profiling systems.
From logs, a fraudster can obtain personal data of compromised user devices that will be useful when imitating the victim’s device. Device data such as type of operating system, Internet browser, screen resolution, timezone, and used language can be easily spoofed. Fraudsters seek to spoof them because it will increase the chance of success for an account takeover (ATO). If an e-commerce website checks only basic data about users who log in, a fraudster who knows the victim’s device data and successfully spoofs them will most likely succeed with an account takeover.
Among data that a fraudster wants to spoof, IP addresses are particularly special. It is almost impossible to spoof the same IP address, so a fraudster will get an IP from the victim’s general area. This is one of the most important resources to buy. Fraudsters do it not only to act similarly to the victim but also for their own security by covering their tracks. In the future, if the police or merchant is searching for the fraudster, they will see the spoofed IP address instead of the fraudster's real one. They can get this IP using one of several technologies, the most popular being a VPN, proxies, and RDP. The first two can be obtained legally and on the dark web, while the third one is available only on the dark web.
The next important material from logs is cookies. These tiny files are generated by websites when a user visits them. Cookies are a great complement to stolen credentials and information about the victim's computer. Cookies can be inserted into browsers using special fraud tools or using dedicated extensions available for some browsers. When a fraudster uses stolen credentials and cookies and changes their settings (browser, operating system, screen resolution, timezone, language) as the real account owner had, they will be recognized as the real account owner for most websites. They must not forget to change their IP address to one from the victim’s area. Now, the fraudster is almost ready to succeed with an account takeover.
Not all stolen accounts bought on the dark web have a pinned payment method. Often, fraudsters have to buy stolen credit cards on the dark web. They can buy them in several places, although the most popular are dedicated shops with stolen credit cards. Less popular are darknet markets (they are like eBay with illicit merchandise), dark web forums, or directly from stolen card vendors using communicators - this option is usually used when two sites of a transaction know each other well. Buying good-quality credit cards is one of the keys to success. In the dark web, business reputation is everything, so fraudsters usually go to the most reputable places.
When a fraudster has all these resources at their disposal, they have more opportunities to commit successful fraud attacks. There are a wide variety of browser-like fraud tools dedicated to committing scams. Some of them can be obtained for free, while some fraudsters pay with cryptocurrencies. Among other interesting things is a tool that can be downloaded for free from a website that sells proxy servers from all over the world. The main task of this tool is to run and organize a collection of proxy servers, which is more helpful than changing it in browser settings. It also has other useful features - it can spoof various browsers, operating system screen resolutions, time zones, and DNS servers. Groups who make such tools usually care for their customers and grant documentation, often with video tutorials on how to use their tools.

Examples of tools for carding that could be bought on one darknet market. A fun fact is that these tools have been available for free for many years, but here, somebody is trying to sell them for USD 5.
Now, when all resources are collected, the fraudster has to configure and set it all up. Everything should be configured to imitate the computer of the victim whose logs the fraudster bought on the dark web. When a fraud tool spoofs the victim’s settings and enables a new IP address, fraudsters usually double-check if everything is running smoothly while using a third-party website.
Once everything is ready, a fraudster can start the attack, which will consist of account takeover and carding. We could say that around 50% of their success depends on the previous steps. Access to resources, tools, quality, and configuration will be one of the deciding factors in the success or failure of a fraud attack.
What else can a fraudster do to increase their odds?
They can pretend to be a typical customer visiting an e-commerce website. Every unusual behavior can be fateful for fraudsters, so they try to look as normal as possible. Fraudsters try to prepare a merchant site for fraud in the process they call the warm-up. Fraudsters won’t avoid interaction with the merchant and its workers - quite the opposite, they will engage as much as possible to appear to be behaving naturally. They will spend a lot of time on the website, checking products, their opinions, details, customer reviews, survey recommended products - everything to imitate a regular customer. Below is a specific description of the warm-up process from one fraud tutorial.
The warm-up begins!
Step 1: Carefully choose your way of entering the targeted site.
Advanced fraudsters carefully choose a way to enter a target site. In this case, they enter an e-shop site directly, not through a link. They have to use a shop domain that matches the country of origin of the stolen data.
For example, if you have stolen an account, credit card, or logs from Germany, you must enter the domain eshop.de instead of eshop.com. Fraudsters know that entering a shop in a different location than the user's can trigger alerts on some anti-fraud systems.
Step 2: Log in to the shop account.
During account takeover fraud, this is a critical moment because if the shop has an anti-fraud system, it could be detected that there is a login attempt from a new device. Even if a new device is detected, the fraudster can still proceed with an account takeover using the account owner's email. But it’s more efficient for fraudsters to imitate victim devices using various resources (as previously mentioned) - this can be very effective if the shop doesn't use sophisticated profiling of their website users. In this case, we assume that the fraudster has imitated the victim's device successfully.
Step 3: Open a new tab with the shop’s menu.
The fraudster duplicates the shop in the browser, and opens a second tab with the shop menu. Then they go to account details and don't close this tab until the end of the process.
This tab has to stay open 'in case of an emergency'. During the next steps, the shop can ask for some cardholder information. Fraudsters should have constant access to all the information that the account owner should have.
Step 4: Evaluate the shopping history on the stolen account
Before any purchase, the fraudster should evaluate the account owner’s purchase history. A fraudster should know details about the account owner's previous orders to avoid a huge disparity between old purchases and desired items. It’s important to remember:
- the type of purchased products,
- their average value,
- shipment destination,
- payment method.
Knowing this, a fraudster will be able to copy the account owner's style of shopping.
Step 5: Act like the owner of the account.
Now it is time for one of the main parts of the ‘warming up the account’ process. A fraudster has to check what was already bought on this account, go through recommended products, check opinions and details, and then add them to cart. If it is not a stolen account but a newly registered one, a fraudster has to browse various similar products. In this step, a fraudster imitates the behavior of a customer who contemplates as they browse the shop.
They look at any product from the order history and click on its recommendation list. If there is no recommendation feature in a given shop, they just browse the same type of product. They check its details, opinions, and questions from other clients, add them to the cart, and repeat this process a few times. Each product should be viewed at random intervals. Add around ten products to the basket. Behave like you are contemplating buying them. Discard half of them and give the remaining items further views, each in additional tabs. Spend 10-15 seconds on each product, looking again at their specifications, etc. Discard products until only 1-2 remain in the basket. At any moment during this step, a fraudster can leave it to rest for some time.
Step 6: Buy one product from the cart.
A fraudster will buy one physical item from the basket (it must be a physical product that will be sent to the account owner's physical address). Although this is a fraudulent payment that uses a stolen credit card, the balance on a stolen account, or other pinned payment methods, it is done to warm up the account. In this step, fraudsters are still acting to increase their credibility for fraud that has yet to be actioned.
If a merchant website detects a new device, a new IP, too many changes on the account (including the most crucial, such as address and contact data updates), and purchases shipped to a new address all within a short time, anti-fraud systems or a merchant employee could recognize that something is wrong. It would be far less suspicious if a package was sent to an old account holder’s address - the one used every time. It would seem that a fraudster has no interest in shipping a fraudulent package to the account owner's home address because it would be of no gain for the fraudster. So, there could be a logical conclusion that it was not a fraudulent payment but a legitimate transaction made by the account owner. This is the legitimization a fraudster is looking for, and it will be useful for the next step.
Step 7: If the payment was successful, check the tracking status.
Even if a payment was successful, the package could be stopped at a later step. A fraudster has to ensure that everything goes as planned and that the package is on its way to the account owner's address. If everything runs smoothly, they can proceed to the next step.
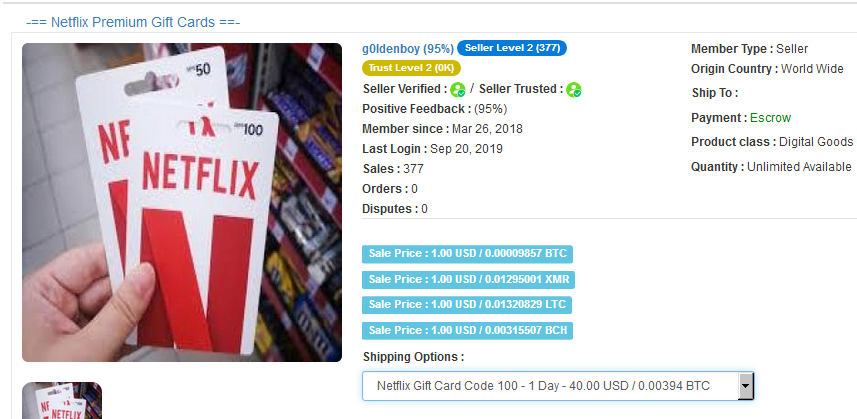
Step 8: Repeat points 1-7, but finish with purchasing a gift card.
They will repeat all previous warm-up steps, but this time, the fraudsters' goal will be to buy their main target - a gift card.
This step consists of all previous warming-up steps, starting with looking at old purchases. In this case, a fraudster wants to buy a digital gift card, and if it is possible, he should start on a product that looks similar to a gift card. If there is no similar product, a fraudster should browse for various digital products such as game keys, coupons, tickets, or various typical gift products. Using this as a way of pointing towards any gift cards, they start to browse various types of this product. There are numerous types of gift cards from different brands, so it depends on the shop assortment and a fraudster-specific goal.
In this step, a fraudster goes through various products and ends up browsing gift cards or other digital merchandise. While looking at each of these products, they can view their details, opinions, and photos, as well as look at similar products. Again, they add around ten of them to the basket - among them will be a gift card, which is their final goal. Each product should be viewed on a different tab. After they gather ten products in the basket, view each of them again for 10-15 seconds and discard them. They continue this until only a gift card is left.
Step 9: Purchase the gift card and commit fraud.
If a gift card order is not accepted, repeat the warming-up (the previous step) after 5-10 minutes. Even if the previous step was already in the new phase of the final stage of fraud, the fraudster could come back to warm up if a payment wasn’t successful.
Giving an account a rest, in this example, for 5-10 minutes, is one of the most popular warming-up techniques. Lack of patience is one of the main enemies for fraudsters because too many changes and actions on an account can raise a lot of suspicions. That’s why the fraudster should wait for some time instead of making a second attempt.
The final phase of the fraud activity: buying gift cards
The next phase after warming up is the actual fraudulent act - the moment when a fraudster makes a fraudulent payment. They can do it using a stolen credit card or payment method pinned to a stolen account. As previously mentioned, the success of this fraudulent action relies on the previous phases - gathering proper resources, configuration, and warming up the website. If this final step doesn’t work, a fraudster can return to the previous phase - for example, they can make another warming-up attempt but more extensively and lasting much longer. If a fraud is successful, they receive a gift card to an email account registered only for that purpose.
There are two main ways of using this gift card - to sell it or use it. Fraudsters can always take a risk and sell it on legal platforms or ultimately sell it on the dark web. Here, we must mention that selling non-working gift cards is one of the most popular scams on the dark web. Yes, fraudsters scam each other very often. It is easier to scam other dishonest dark web users than to fraud an online shop, so many fraudsters choose this method of making money. Most dark web citizens know that it is hard to sell stolen gift cards to somebody who doesn't have a good reputation as a seller. For this reason, in the dark web you can find wholesale buyers who purchase stolen gift cards from other fraudsters and then resell or use them.
The other option is to use gift cards to get other, more expensive goods. There are various types of gift cards; some can be used for a variety of products, and others are only for computer games. It is always easier for fraudsters to work with digital goods because, in this case, they don’t have to organize a safe home address to receive fraudulent packages. Furthermore, there is always a risk that fraudulent purchases of gift cards can be discovered and the gift card subsequently deactivated, therefore, fraudsters have to hurry to use or sell them.
The final question is, what do fraudsters do with the account that was used for fraudulent activities?
They can wait several days to see if something happens, such as changing passwords. If not, the account owner may remain unaware that something suspicious has occurred, and a fraudster can try to make another fraudulent attempt using this account. If a fraudster commits one fraudulent act using this account, what’s to stop them from trying again?
We can't share all the details here because we don't want to help fraudsters with our knowledge. If you want to learn how to protect your business from the latest fraudulent tactics and how our fraud detection powered by AI and darknet insights can help, please contact us.


